Blog

Cloud Security Posture Management
Our recent blog on cloud security posture management explores some of the main uses cases of CSPM solutions, highlighting their benefits and how to get the most out of them.

Preparing for the NIST Cybersecurtiy Framework 2.0
The cybersecurity industry is on the cusp of a big change, one that’s going to cause many organizations to reevaluate their practices and reshape how we communicate core aspects of what we

Automating your Security with Policy Orchestration
Automating your Security with Policy Orchestration In today’s digital age, cybersecurity is more important than ever before. With cyber threats becoming increasingly sophisticated and digital landscapes evolving rapidly, it’s crucial to ensure

Best Practices for the NIST Cybersecurity Framework
Network Security, user authentication, incident response, . . . Sometimes cybersecurity can seem like an endless stream of complex technical topics and an endless laundry list of things that need to get

What is Cybersecurity
What is Cybersecurity: It’s increasingly important to have a basic understanding of what cybersecurity is. Our lives become increasingly reliant on technology, and hackers are becoming increasingly dangerous and capable. If you

How to Spot a Phishing Email
How to Spot a Phishing Email The email inbox is a battleground. Most of us are flooded with hundreds of emails fighting for our attention. Even worse, a disturbingly large portion of these

The Key Principles of Zero Trust Cybersecurity
Cybersecurity teams are often trapped in cycles of reactivity, scrambling to respond to the latest issue. To be truly effective, we need a proactive security strategy that limits the overall attack surface.
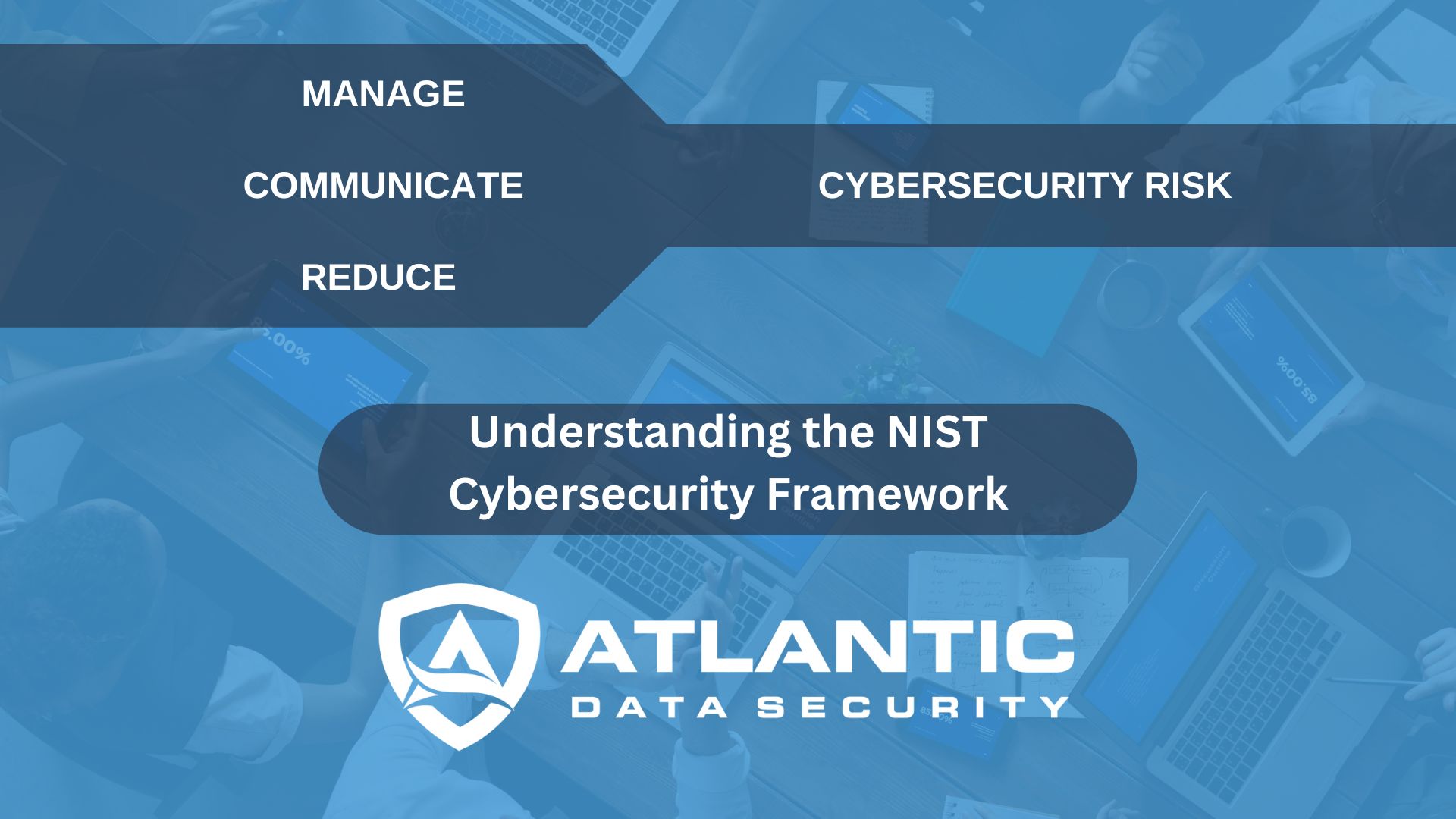
What is the NIST Cybersecurity Framework?
Introduction: How can security leaders communicate with other company members who don’t share their technical experience? How can a CEO understand how exposed their company might be to cyber risk? First published

How AI is Reshaping Cybersecurity
Artificial Intelligence (AI) enables cybersecurity companies to discover and address security risks more quickly than ever. However, it is essential to understand the many risks that AI poses to the cybersecurity industry.

Top 5 Must-have Cybersecurity Certifications for New Professionals
It is no secret that there are a vast array of certifications available in the cybersecurity industry. From CompTIA to CISSP, to CISA, how would you know which ones are worth getting?

Multifactor Authentication: What is it? How to use it?
Ensuring seccuring access to accounts, networks and devices has never been more critical. Threat actors are increasingly innovative and sophisticated, getting into places they don’t belong. Cybersecurity professionals and leaders have long

Best Practices for a Secure Password
Understanding and implementing best practices for password security is essential. Safeguarding sensitive information demands a keen understanding of the vulnerabilities associated with passwords. Strong passwords serve as the first line of defense

Tackling the Business Risks of AI
Are we unknowingly opening Pandora’s box with AI (Artificial Intelligence) in our businesses? Recently, Atlantic Data Security teamed up with Fortra for an insightful webinar exploring this very question. What are the immediate

Over 178,000 SonicWall Firewalls are publicly exploitable to years old bug
Yesterday, Bishop Fox released research where they found that at least 178,000 SonicWall firewalls devices were vulnerable to at least one of two critical exploits that had been discovered over a year ago.

Content Zero Trust
As malware becomes increasingly sophisticated and harder to detect, the need for robust cybersecurity has never been more critical. Zero Trust has emerged as a powerful model in this landscape, primarily focusing

 Why ADS
Why ADS Executive Team
Executive Team Careers
Careers Certifications
Certifications Application Security
Application Security Cloud Security
Cloud Security Cybersecurity
Cybersecurity Data Security
Data Security Endpoint Security
Endpoint Security Professional Security Services
Professional Security Services Network Security
Network Security Perimeter Security
Perimeter Security Staff Augmentation
Staff Augmentation Training
Training Blog
Blog