Introduction:
How can security leaders communicate with other company members who don’t share their technical experience? How can a CEO understand how exposed their company might be to cyber risk?
First published in 2014 and recently overhauled at the start of 2024, the NIST Cybersecurity Framework (CSF) was developed to bridge the gap between detailed technical security know-how and business expertise to communicate and coordinate risk management and security strategy.
Over the past decade, it has served as a valuable baseline for thinking about and communicating cybersecurity matters within the industry and with outside stakeholders. But it can be a daunting tool to begin to understand and utilize.
Let’s review how the NIST Cybersecurity Framework allows individuals from all backgrounds to communicate effectively about cybersecurity. From high-level business principles to detailed technical concepts, the Framework lets everyone engage effectively in the cybersecurity discussion.
Table of Contents
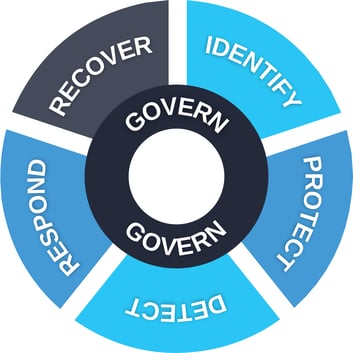
Framework Core
The Framework Core covers the entire cybersecurity domain and divides it into five discrete components called Functions. These Functions are the backbone for managing cybersecurity risks. Each NIST function is further broken down into categories and sub-categories, providing an increasingly granular analysis and catalog of an organization’s cybersecurity practices. The Framework includes Informative References like existing standards and best practices to guide implementation. These components create a comprehensive yet flexible roadmap, allowing organizations to plan their cybersecurity approach to align with their unique needs and objectives.
- Govern – The Govern function is the central function of the framework, and foundational for for effective cybersecurity management. It informs organizations on how to prioritize and achieve measures called for by the other five functions. By developing the necessary context around the organization’s missions, stakeholders, and regulatory and legal requirements, the governance function enables effective cybersecurity guided by business risk management. The six categories of the Govern function include:
- Organizational Context;
- Risk management strategy
- Roles, Responsibilities, and Authorities
- Policy
- Oversight
- Cybersecurity Supply Chain Risk Management
- Identify – The Identify function is the foundation for effective cybersecurity management. It focuses on developing an organizational understanding to manage cybersecurity risks related to systems, assets, data, and capabilities. This function helps organizations understand their business context, the resources that support critical functions, and the associated cybersecurity risks. This enables organizations to focus and prioritize their efforts in line with their risk management strategy and business needs. The main categories of the Identify function are:
- Asset Management
- Risk Assessment
- Improvement
- Protect – The Protect function aims to develop and implement appropriate safeguards to ensure the delivery of critical infrastructure services. It supports the ability to limit or contain the impact of a potential cybersecurity event. This function encompasses the following categories:
- Identity Management, Authentication, and Access Control
- Awareness and Training
- Data Security
- Platform Security
- Technology Infrastructure Resilience
- Detect – The Detect function helps develop and implement activities that identify the occurrence of a cybersecurity event. Detection enables the timely discovery of cybersecurity events. The Detect categories are:
- Continuous Monitoring
- Adverse Event Analysis
- Respond – The Respond function focuses on developing and implementing appropriate activities to react to a detected cybersecurity event. This function is crucial for managing the actions taken during and after a cybersecurity event, ensuring that the organization can recover and learn from these events. The Respond categories are:
- Incident Management
- Incident Analysis
- Incident Response Reporting and Communication
- Incident Mitigation
- Recover – The Recover function aims to develop and implement activities that maintain plans for resilience and restore any capabilities or services that fail due to a cybersecurity event. This function ensures an organization can bounce back and restore its services after a cybersecurity incident. The Categories of Recover are:
- Incident Recovery Plan Execution
- Incident Recover Communication
Tiers
The Tiers in the NIST Cybersecurity Framework allow security teams and business leaders to understand their security maturity, resources, and gaps. They provide a mechanism for organizations to gauge the maturity of their cybersecurity practices. Organizations take the Framework one sub-category at a time and determine which tier best describes their performance in a given sub-category. The informative References and Outside expertise are both helpful in accurately and impartially determining an accurate tier level.
- Tier 1: Partial – Tier 1 Sub-categories are not formalized and are managed in an ad hoc, sometimes reactive manner. There is limited awareness of cybersecurity risk at the organizational level, and the organization does not have processes to convey and distribute necessary information on the given topic. Generally, the organization is unaware of the cyber supply chain risks of the products and services it provides and uses.
- Tier 2: Risk-Informed – Organizations have risk management practices in place on Tier 2 sub-categories but may not be established as organizational-wide policy. There is an awareness of cybersecurity risk at the organizational level, but an organization-wide approach to managing cybersecurity risk has not been established. Cybersecurity information is shared within the organization on an informal basis. The organization is aware of the cyber supply chain risks associated with the products and services it provides and uses but does not act consistently or formally upon those risks.
- Tier 3: Repeatable – Tier 3 sub-categories represent when an organization has formal risk management practices and policies. There is an organization-wide approach to managing cybersecurity risk. Risk management policies are regularly updated based on threat intelligence and business needs.
- Tier 4: Adaptive – The Adaptive tier represents the highest level of maturity in a cybersecurity topic. In this tier, organizations have adapted their cybersecurity practices based on lessons learned and predictive indicators derived from previous and current cybersecurity activities. There is an organization-wide approach to managing cybersecurity risk that uses risk-informed policies, processes, and procedures to address potential cybersecurity events.
Profiles
The Framework Profile serves as a tool to understand an organization’s alignment with the Cybersecurity Framework and to leverage that understanding to develop a roadmap toward reducing cybersecurity risk consistent with the organization’s business goals, legal and regulatory requirements, and risk management priorities.
- Current Profile – When an organization performs a risk analysis based on the NIST Cybersecurity Framework, they catalog their performance across the various functions and categories using the Tiers. This summary serves as an organization’s Current Profile, a baseline for understanding the organization’s current cybersecurity posture.
- Target Profile – Organizations can similarly use the Tiers and Core to specify the required level of security maturity that their business and risk tolerance level requires. They can prioritize which subcategory targets are more important. This process creates the Target Profile for the organization. By comparing the Target Profile with their Current Profile, organizations can perform a gap analysis and identify which aspects of their security posture they must focus on.
Conclusion:
Organizations can formalize their understanding of their current security posture and goals by developing a current and target profile. The Framework categories help break down the resulting improvement project into discrete, manageable, and measurable goals. Rather than having 1 set methodology, there are several considerations and best practices when leveraging the NIST Cybersecurity Framework. We’ll discuss these in more detail in our next NIST Framework article.
At Atlantic Data Security, our seasoned security team has decades of experience performing risk assessments and communicating the findings to bridge the gap between the security team and leadership. Contact us when you are ready to improve your cybersecurity strategy and communication.